various bits and pieces describing Android Auto protocol (aka AAP) (aka GAL) and headunit emulator binary
There’s headunit integration guide found in the abyss of google cache, which might provide high-level overview of AA features. It is a bit outdated (version 1.3, while current version seem to be 1.6)
mirror there: huig13_cache.html
Google provides desktop headunit emulators binaries for testing, described there: https://developer.android.com/training/cars/testing. In this descriptions I will refer to the Linux version. They provide x86_64 binaries, statically linked with OpenH264, PortAudio, OpenSSL. I want to have AArch64 device working as headunit, so I have this slightly crazy idea that instead of reimplementing AAP protocol use their binary under x86_64 user mode emulation, and move all heavy processing (video, audio and encryption) out of it through IPC to native side. That their binary is statically linked causes a problem though, so first I need to patch their binary to make it import these symbols dynamically, so I can LD_PRELOAD my own stubs instead of real library (and these will talk over IPC to native ARM side where real libraries will reside). This is done using LIEF: destaticizer.py. Note that when replacing C++ functions you need to use llvm libc++ ABI, not the GNU libstdc++.
Their official emulator binary works only over TCP, not over USB as Android Auto is normally used. (their guide talks about using adb to bridge it, but proxy localhost:5277 with socket directly to phone and it will work over network too) Protocol is the same however, and stream data is just pushed through bulk endpoints. It just needs to be initialized through Android Open Accessory protocol, but that is publicly documented.
Here’s a simple program using libusb to proxy AAP over USB to Unix domain socket: apserver.c. (and then you can use socat to connect it with emulator binary, or LD_PRELOAD some stub to redirect their TCP socket)
AAP protocol uses protobufs to exchange most of structured data. Their description can be extracted from binary in human readable format (extracted using pbtk):
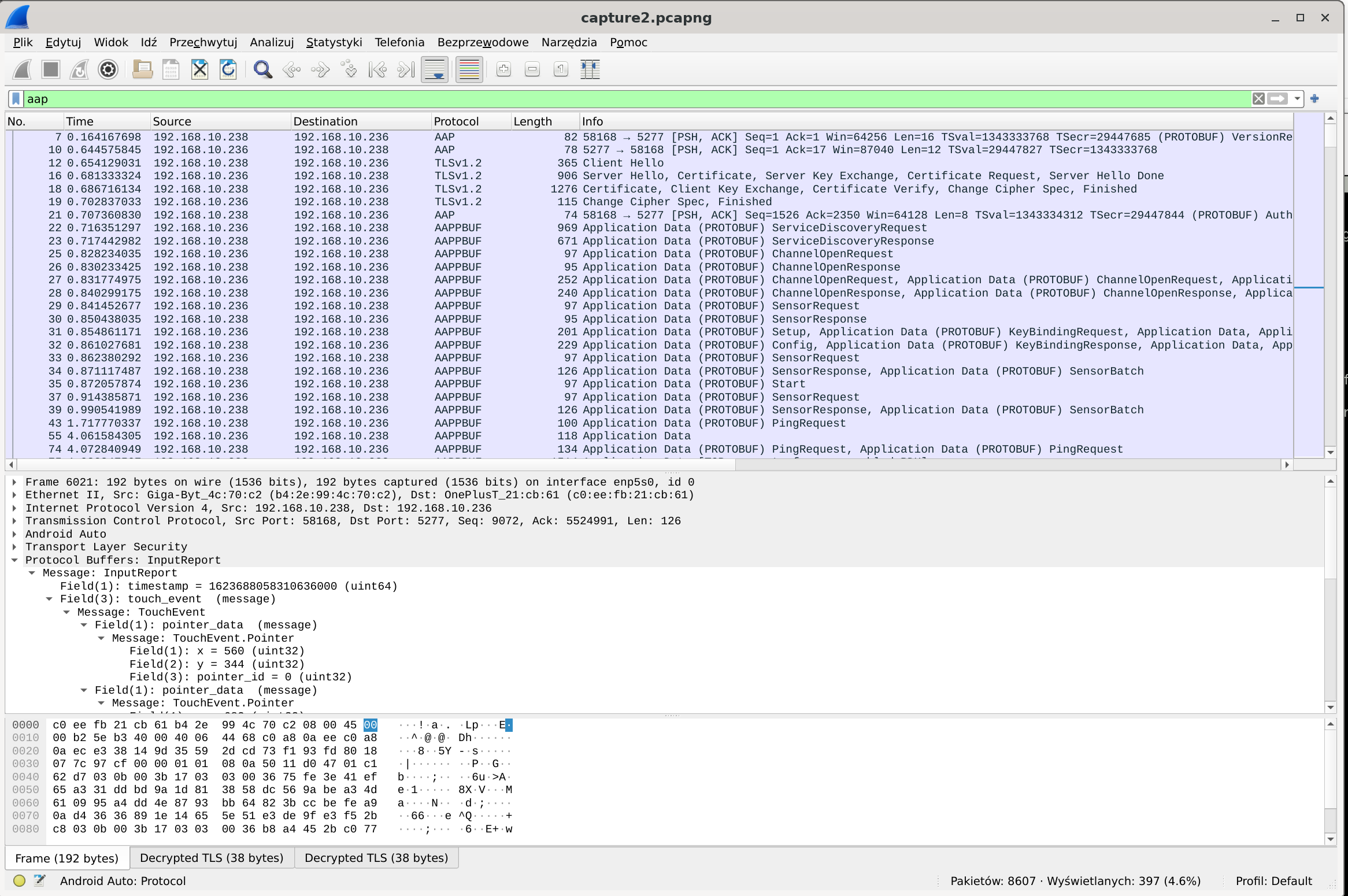
I also made simple wireshark dissector for AAP: androidauto.lua.
Almost all Android Auto communication is encrypted with TLS, so you need to dump session keys so Wireshark can dissect it (just point Wireshark to key logfile as usual). You also need to configure Wireshark protobuf dissector to add paths to protobuf files linked in above section. I think it should work fine for basic framing, sensor and input service, but it needs more work to extract ids from ServiceDiscoveryResponse to be more correct and work for other services. To dump session keys from official headunit emulator, see emulator binary hacking section to export their internal SslWrapper, and then you can use this stub to use external OpenSSL and capture keys: ssl_preload.cpp
